
SITA cyber-attack part II: report
Task It can be useful to look at cyber-attacks in the news to prepare ourselves for similar events. While the available information may be lacking,
Join me as I undertake my Master’s of Cyber Security
I’m Luke Hally, I’ve been working in the digital sector for over 25 years across web development, IoT and product ownership for startups, enterprise, government and global brands. Building on this I’m currently undertaking a Master’s of Cyber Security Leadership at UNSW. I have a passion for aviation and believe it is a sector ill prepared for the connected future it faces, so I have focused my assessments on aviation cyber security where possible, with a goal of becoming an aviation cybersecurity SME.
Blog categories are broken down by the courses as I take them and tags will be by interest area.
Find out more about me in my intro blog.

Task It can be useful to look at cyber-attacks in the news to prepare ourselves for similar events. While the available information may be lacking,

Task Research recent cloud security incidents with prominent media coverage, and identify one to study for this exercise. For the incident you select, you will

Task In this assessment you will consider the policy implications of your new Cyber Strategy, highlighting and explaining two policy statements which support the strategy.

Task As we have previously discovered, cybersecurity in the aviation sector is an emerging field. In light of other countries introducing specific aviation cybersecurity regulation

Around the globe, car rental companies rely on technology for operating in an efficient and responsive manner. Here at RideWell we use a website and

Continuing on from our recent presentation to make a case for advanced cyber risk monitoring, RideWell’s management team would like your view and recommendation on

The cyber security industry is increasingly recognising that they need to adopt mature risk management and monitoring practices in order to elevate the profession and

An area of the Privacy Act that could be improved is consent in regards to Privacy Principle 3 – collection of solicited personal information. The

The Notifiable Data Breach scheme seemed so simple back when I started this Master’s degree. Now we are exploring its intricacies in my Cyber and

In this final assessment I looked the current and emerging cyber security vulnerabilities of financial inclusion. In answering this question I looked at what financial

An overview of Red Teaming and the role it plays in cybersecurity. Who should use it, how does it differ from penetration testing and is

What distinguishes cybercrime from other types of crime, and why is this important to the cyber security profession? When considering what distinguishes cybercrime from other

Introduction: The aviation sector Aviation is an important sector, employing 58 million people, contributing $2.4 trillion to global GDP and annually carrying 3.3 billion passengers

What is “hacking back”, what are its advantages and disadvantages, and what role does it play in cyber defence? Hacking back is “the ability to

This was my final assessment for the cyber ethics course, it was a great topic that brought together the ethical theories with a real world

The various normative ethical theories (deontology, utilitarianism, agent based) provide different ways of viewing the world and could lead to justifiably opposing outcomes. Let’s look

In 2019 researchers from Security Without Borders discovered the Exodus malware had infected almost 25 apps in the Google Play Store (Franceschi-Bicchierai, 2019), further investigation

The ethical considerations of cybersecurity professionals towards the public include: individual privacy vs public security; individual security vs availability of public goods; transparency vs preserving

One of the the things that we need to consider when making ethical decisions is the impact the decision will have, not just now and

Equifax is one of the world’s largest credit reporting agencies (CRA), creating credit reports from consumer data which is sold to third parties. Being high

In looking at the ethics of a technology, we need to assess whether it is value laden or neutral. If a technology impacts on the

We all know that we should use unique passwords for each service (Facebook, Netflix etc) we use. This is to prevent a credential stuffing attack,

Quantum computers have potential for great advances in our understanding of the world, and it may be happening sooner than we think with recent advances

The ‘war on encryption’ – law enforcement attempting to bypass or limit consumer level encryption – is a global issue with many platforms utilising encryption

Looking in more detail at privacy this week. I encountered privacy in my first course, Foundations of Cyber Security. It had a profound impact on

We see lifecycles everywhere, product lifecycles, software development lifecycles, data lifecycles. They are a useful way to gain a high level understanding of something and

Symmetry and asymmetry is something we see a lot of in cyber security. We break symmetry with passwords and authentication – making it easy for

The data lifecycle is a useful tool to understand all of the stages data goes through. This can include: what is collected; how it is

The start of a new course this week, Data Security and Privacy. I’m looking forward to this one, we learn how to actually hack into

“ Social engineering is an extremely effective technique used by hackers worldwide to compromise internal systems and proprietary information assets. In fact, it’s one of

On 29 April 2018, NewCorp journalist, Annika Smethurst, reported that the federal government was wanting to expand its powers to spy on Australian citizens. This

I’ve had a couple of opportunities to apply what I have learnt in the real world this week. Estimating Attacker Power This degree has affected

We authenticate to solve real world problems. For example I want me to be able to access my bank account and I don’t want anyone

This one was from a few years ago, but with biometrics becoming more and more prevalent I think it’s relevant today. A successful voiceprint hack

Authentication is proving who you are. Not to be confused with authorisation, which is having permission to access or use something. In security we often

Thanks to my involvement in fintech, I’ve been around the edges of bitcoin and blockchain for a while Traditional money relies on a trusted third

There’s a lot to remember about hashes, so I’m bringing the definitions into one place as a reference. Term Definition Avalanche effect Small changes in
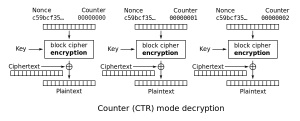
DES (Data Encryption Standard) and AES (Advance Encryption Standard) are both block ciphers. The message is broken into blocks and each block is encrypted and

What are type I and type II errors? They sound fancy but are quite simple to understand and are a good way to look at

Encryption is the glamourous part of confidentiality, today we will look at hashes. We’ll cover regular and cryptographic hashes, a bit of history then we’ll
© Copyright 2021, Luke Hally